International Covid impact research platform
Universiteit Antwerpen
Scientifically substantiated personal advice on Covid measures for minorities.

Scientifically substantiated personal advice on Covid measures for minorities.
Some project highlights
Worldwide used, tailor-made survey platform
Scientific advice to minorities
Complex scientific calculations and reporting
High performance with more than 100.000 pageviews on 1 day
Launched in 25 countries simultaneously
Multi language support for uncommon languages like Chinese, Amharic, Arabic, Hindi, Kinyarwanda, Swahili, …
Limited budget but scalable, no licensing fees per survey, user or submission
University of Antwerp owns its own data, data storage is on EU infrastructure
Maximal privacy, data anonymization and security
Survey builder
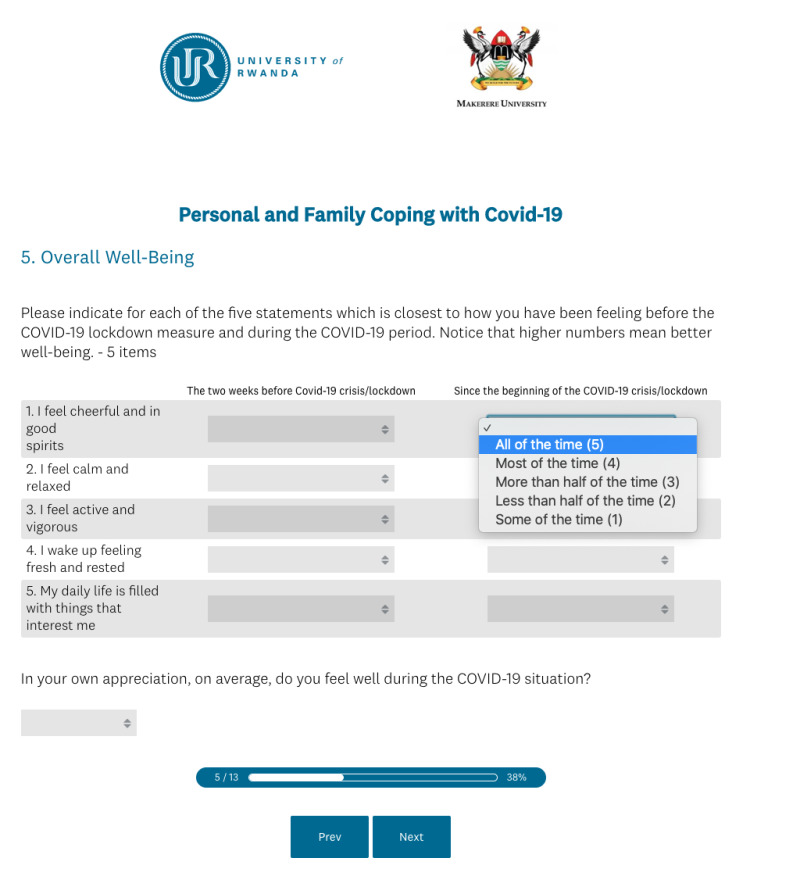
We have provided a survey (form) builder where steps with questions can be configured by the administrator.
The created forms are checked for consistency before we use them as a basis for further analysis.
At the end of the survey, we generate a report where general advice is shown to the respondent, based on the submitted answers.
An email address is optionally requested to check whether the same person has filled in the survey multiple times. Here we show a link to a privacy policy page to explain what happens with the stored data and that a questionnaire respondent can always choose to be “forgotten” by following a certain procedure resulting in erasing the record(s) with his or her email-address from the database.
Detailed personal feedback
We have built a custom analytical component.
This intelligent component is based on scientifically substantiated calculation methods provided by the University of Antwerp.
It uses a collection of submissions to create quintiles/centiles as a basis for personal advice.
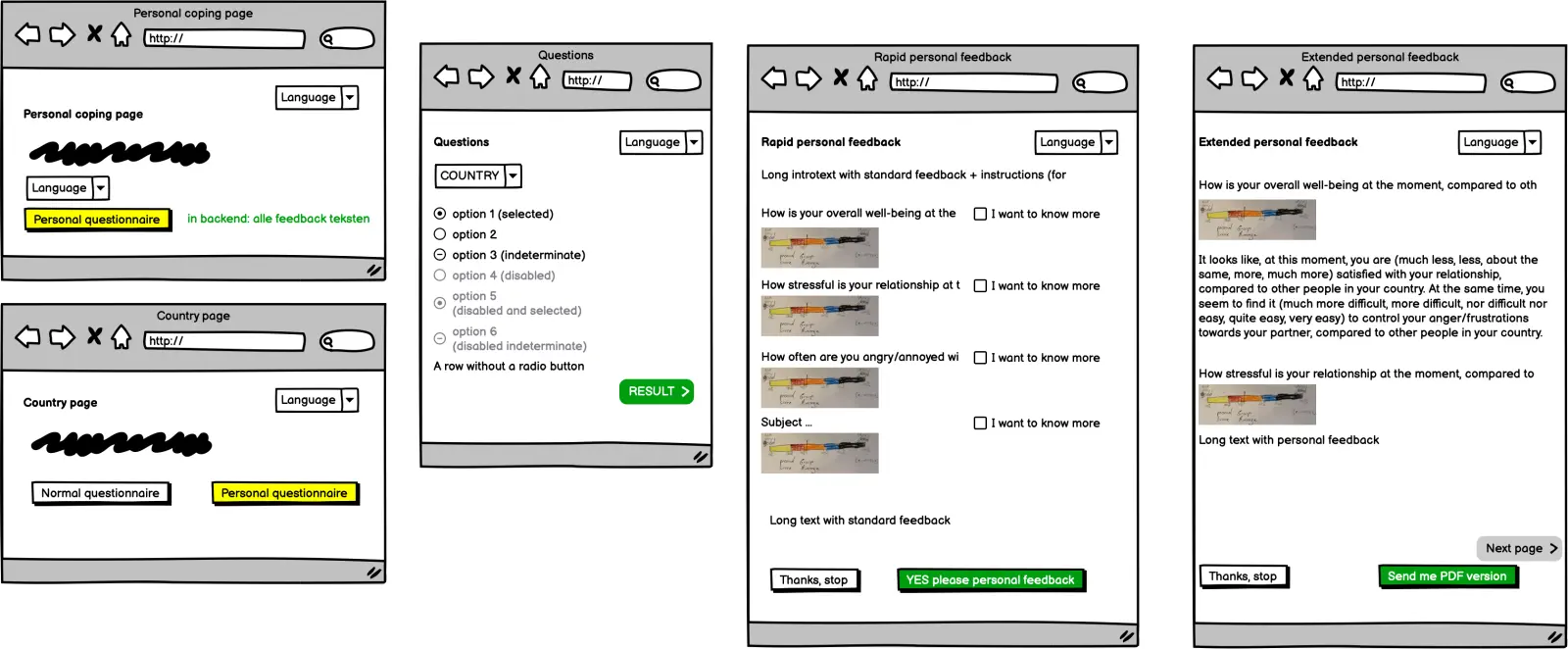
The platform can generate two types of personal feedback
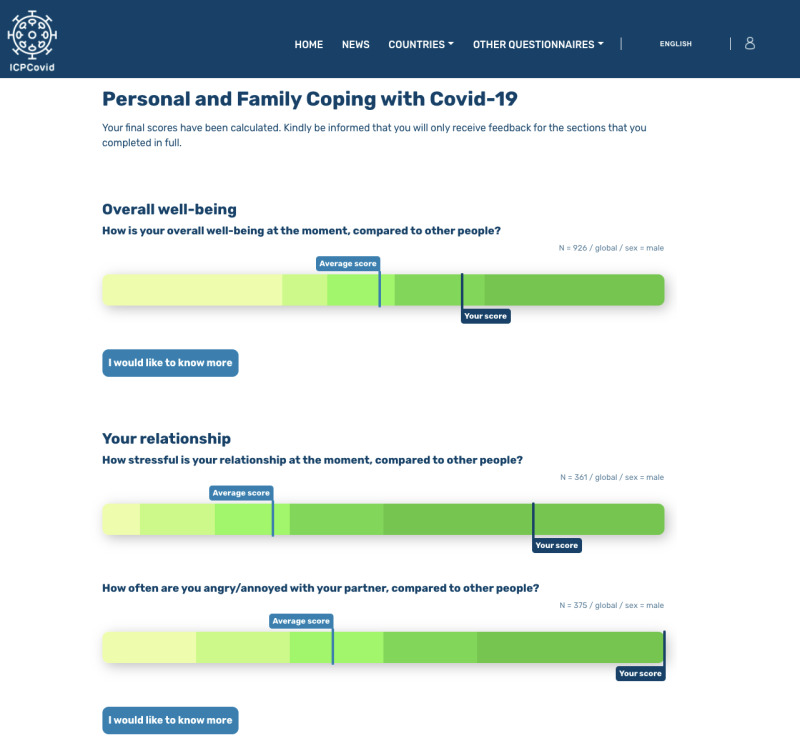
Rapid personal feedback
Each individual submission generates a personal advice by comparing it with a saved analysis. This personal advice is displayed per category in a bar (Personal Score / Group Average / Number of submissions)
Extended personal feedback
From the "Rapid Personal Feedback" a visitor can choose in which categories he wants to learn more: these choices are saved.
On the next page, the visitor receives personalized feedback for the selected categories and associated tips in the form of a few sentences of text. These texts can be entered into the system by the administrator and translated (translations can differ per country).
The visitor can enter his email address to also receive the detailed personal report in a PDF document by email.
Privacy and obscuring personal and demographical data
Outline: we provided a complex of implementations that as a whole allows for:
Maximal privacy of questionnaire respondents, specifically the highest inability of linking an identifiable individual with a particular questionnaire submission
“Data anonymization” applied to the raw questionnaire data, with the final product to be used by the scientists involved to construct their analysis
The least amount of persons possible that have access to the server and database containing raw data
Respondents are asked to enter their email-address if they want to be invited to repeat-take the questionnaire and/or if they want access to an evolution in their psychosocial evaluation.
We split the two usages of the email-address:
We store the email-address in a separate table, along with demographical data like age-category, sex, and country code, that has no connection whatsoever to the questionnaire data
We use the email-address as the basis for a unique identifier (technically: running it through a cryptography algorithm that creates a non-human-readable string of 32 alfanumeric characters that cannot be “reversed” to recreate the email-address upon which it was built).
The stored data will be scrambled, unreadable, and quasi-irreversible obfuscation of an email-address provided by a respondent during his or her filling out of the questionnaire.
Security
Secure Access
Out of the box, account passwords are encrypted--salted and repeatedly hashed--when they are stored in the database. We also support a wide variety of password policies such as minimum length, complexity, or expiration. Industry standard authentication practices are also supported including SSL and 2-factor authentication. Many single sign-on systems can be added including LDAP, Shibboleth, OpenID, and SAML.
Granular User Access Control
We give administrators complete control over who can see and who can modify every part of a site or platform. This is operated based on a system of extensible user roles and access permissions. Administrators can create user roles and give them specific, limited permissions. For example, a site might need an author role that can create and update content, but not publish or delete it--permissions reserved for the editor role--while administrative settings are reserved for a separate role entirely. Authenticated users can be assigned any number of roles, and their permissions are cumulative. Menu links and features are automatically hidden from users who do not have appropriate access.
Database Encryption
In high security applications, we provide extremely strong database encryption. When whole-database encryption is not desired, very high granularity is available to protect more specific information: user accounts, specific forms, and even the values of specific fields can be encrypted in an otherwise plaintext database. The encryption system can be configured to pass the strictest PCI, HIPAA, and state privacy laws, including offsite encryption key management.
Preventing XSS, CSRF, and other malicious data entry
The implemented Form API ensures that data is validated and scrubbed before entry in the database. The system tests that user-entered data--and even the form fields themselves--match prescribed, expected formats and values. Tokens are injected into each form as it is generated, to protect against potential CSRF attacks. The database abstraction layer performs additional security checks on data as it is written to and retrieved from the database.
Brute Force Detection
We implemented protection against brute-force password attacks by limiting the number of login attempts from a single IP address over a predefined period of time. Failed login attempts are logged and visible via the administrative interface. We can also allow administrators to ban individual IP addresses and address ranges.
Mitigating Denial of Service (DoS) Attacks
Our frameworks extensible cache layer comes pre-configured with basic page, Javascript, and CSS caches. The system supports deep integration with performance technologies such as Memcache, Redis, Varnish, and many popular CDN services. Individual components are typically cached as well, and granular expiry is a common feature. This multi-layered cache architecture is extremely resistant to high volumes of traffic, and makes this PHP framework the system of choice for some of the world’s highest-traffic websites.
Addresses OWASP Top 10 Risks
We included features that address all of the Open Web Application Security Project’s top ten security risks, a list of the most commonly seen risks in practice.
Web hosting
The server is located inside the EU (Netherlands), a Tier 3 data centre. We take strict security measures to prevent misuse of and unauthorized access to personal data. This way we ensure that only the necessary persons have access to the data, that access to data is protected and that our security measures are checked regularly. In addition, we use SSL certificates for the secure transfer of data.